Asset Management Real-time device and asset tracking



Live Asset List
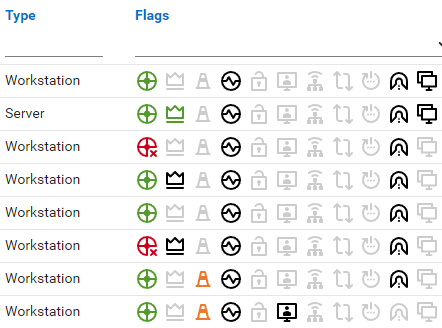
Key Information
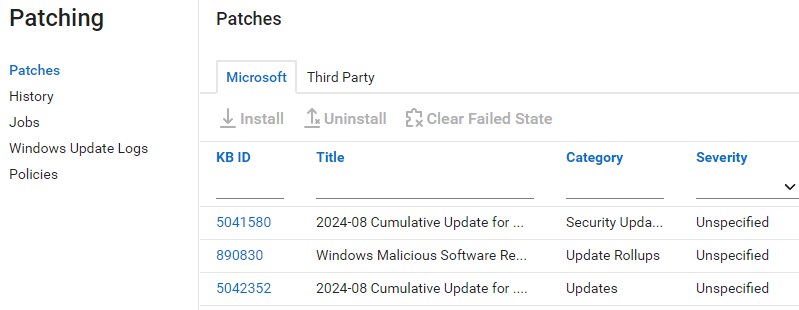
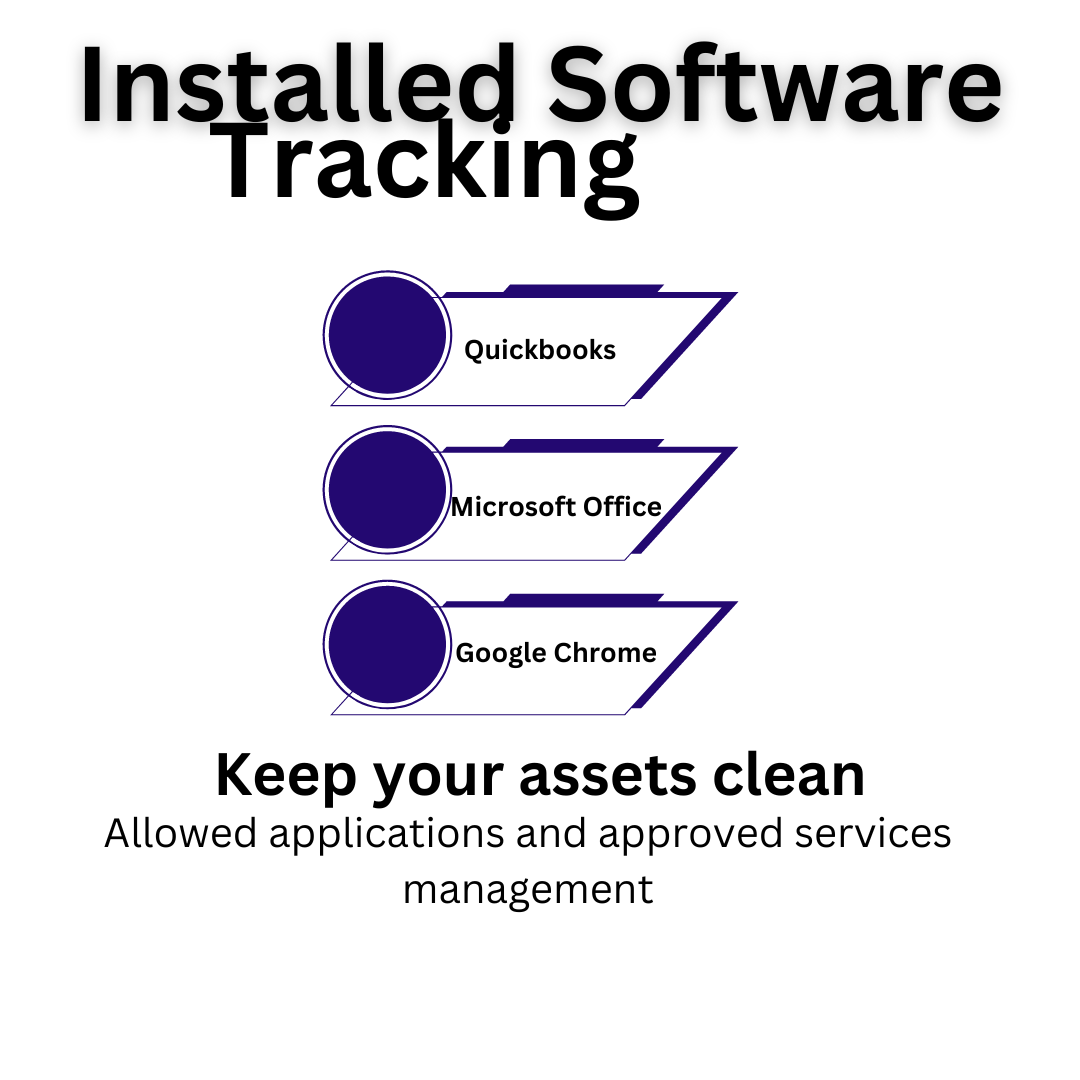
*Installed Microsoft and 3rd Party Security Patching
*Deploy software and preferences company wide
*Enforce OS level preferences for security and compliance automatically
*Available as a service and Co-Managed
Key Elements for Successful Asset Management
Role-Based Access Control (RBAC): Implementing RBAC ensures that users have access only to the information and systems necessary for their specific roles. This minimizes the risk of unauthorized access and reduces the likelihood of security breaches by limiting permissions based on job functions.
Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to verify their identity through multiple authentication methods, such as passwords combined with biometric data or one-time codes. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
Regular Audits and Monitoring: Continuous monitoring and periodic audits of access rights are essential to maintaining the integrity of access management. Regularly reviewing user access helps identify and address any discrepancies, unauthorized changes, or outdated permissions, ensuring that only authorized personnel have access to critical systems and data.

