Cyber Security Solutions Services tailored to help businesses protect their assets
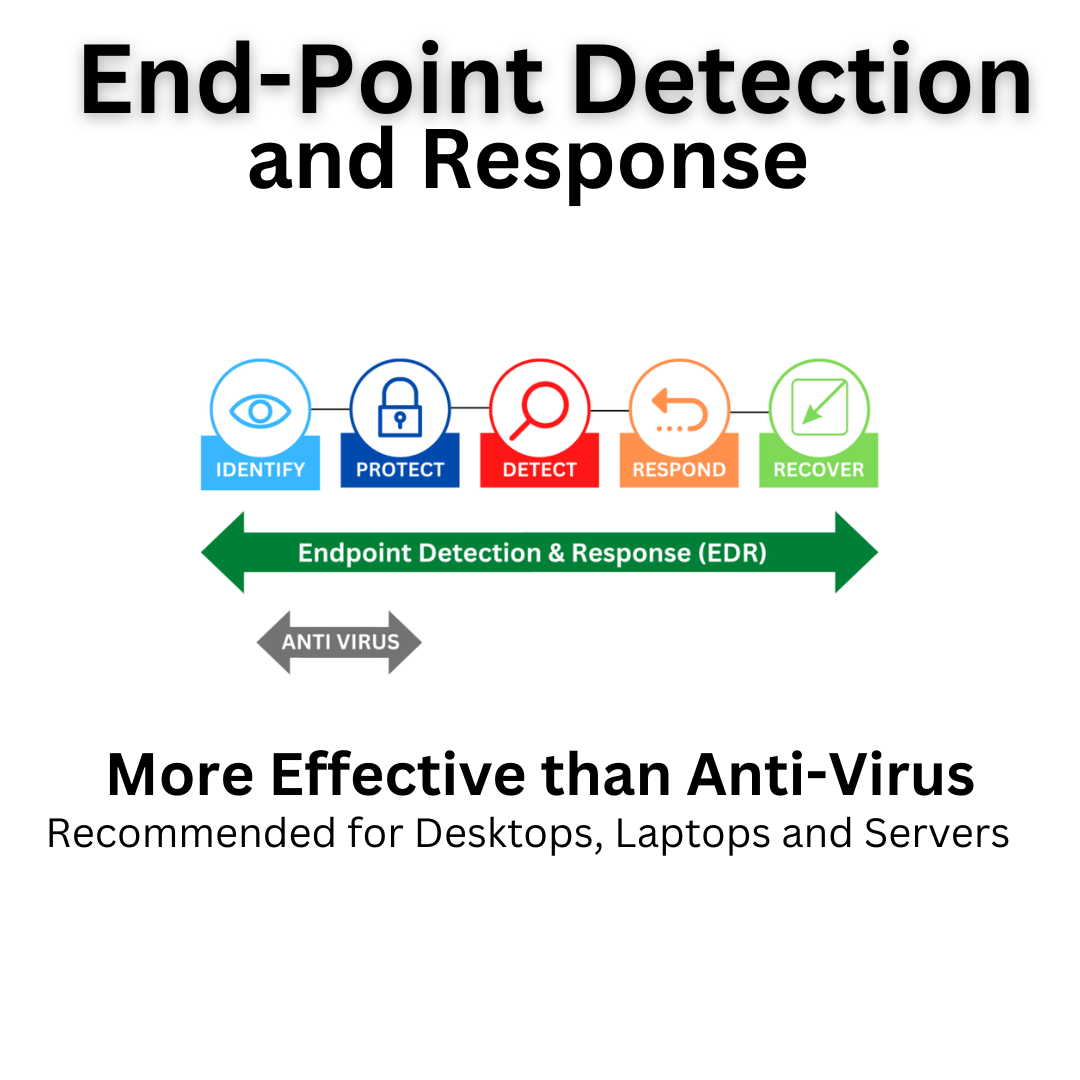
Proactive Threat Detection and Response: Endpoint Detection and Response (EDR) tools continuously monitor and analyze activity across all devices, enabling quick identification and neutralization of threats before they can cause significant damage.
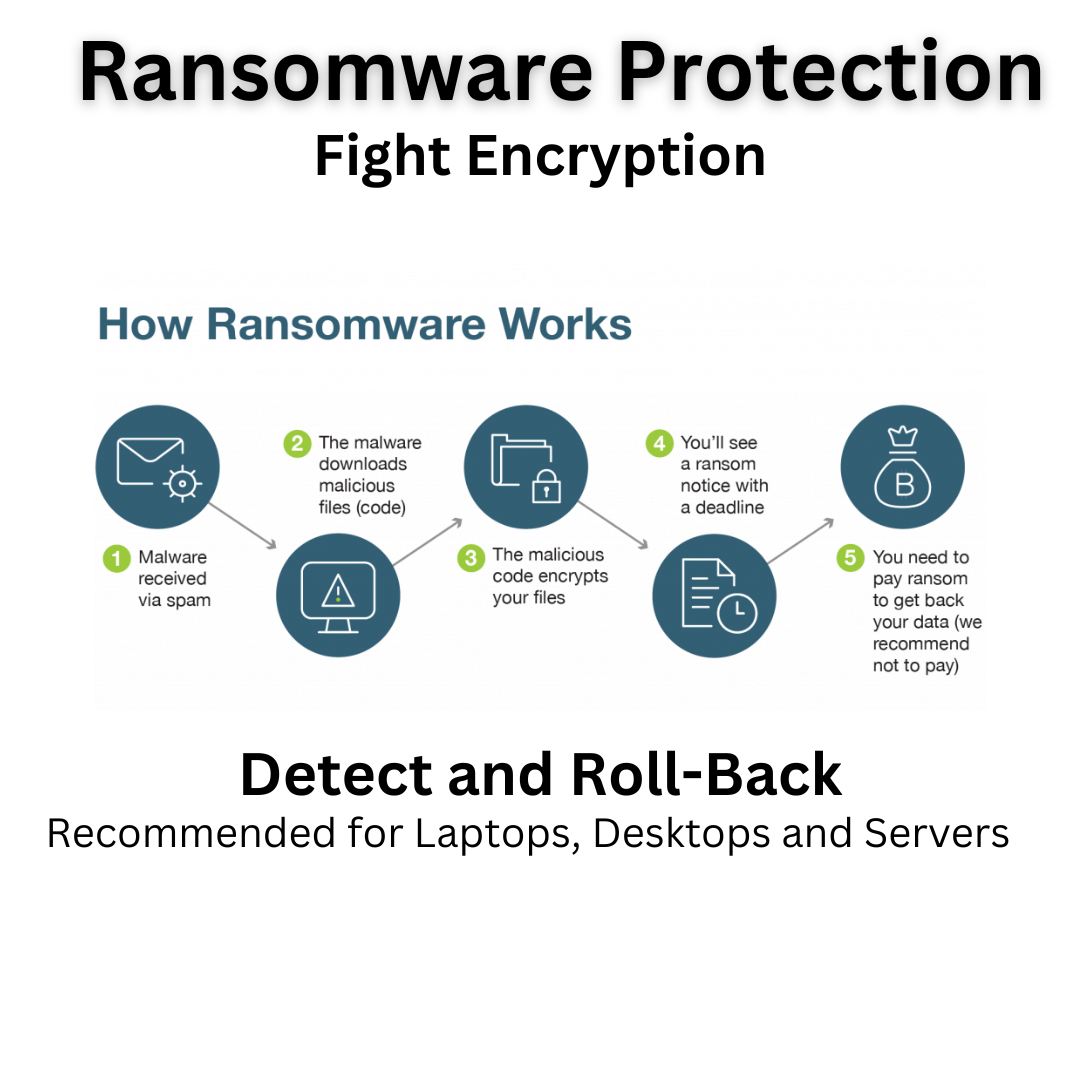
Critical Defense Against Ransomware Attacks: Ransomware protection software safeguards your business by detecting, isolating, and preventing ransomware attacks, ensuring that your data remains secure and accessible, even in the face of evolving cyber threats.
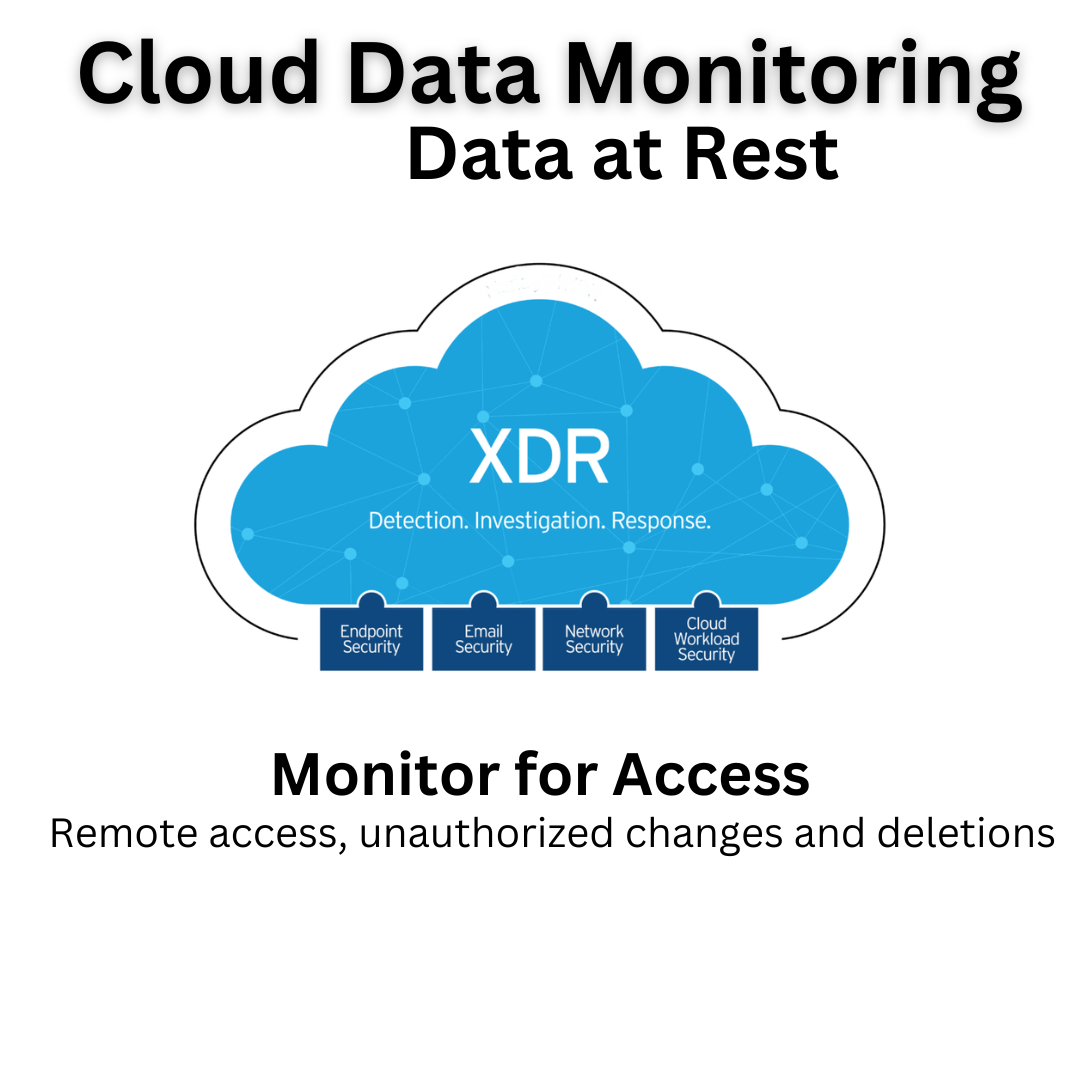

Protecting Sensitive Data at Rest: Cloud application security ensures that your data stored in the cloud is encrypted and protected against unauthorized access, safeguarding sensitive information and maintaining compliance with data protection regulations.
Ensuring Data Availability and Recovery: Regular backups of your cloud data provide a crucial safety net, allowing you to recover important information quickly in case of accidental deletion, cyberattacks, or system failures, ensuring business continuity.


Enhanced Security with Multifactor Authentication (MFA): MFA adds an extra layer of protection by requiring multiple forms of verification before granting access, significantly reducing the risk of unauthorized access and protecting your business from potential breaches.
Ongoing Protection through Software Patch Management: Regular patch management ensures that all software is up-to-date with the latest security fixes and improvements, closing vulnerabilities and preventing cyber threats from exploiting outdated or unpatched systems.

Safeguarding Critical Data with PC Backup and Replication: Regular backups and replication of PC data ensure that important files and documents are securely stored and can be quickly restored in the event of hardware failure, accidental deletion, or cyberattacks.
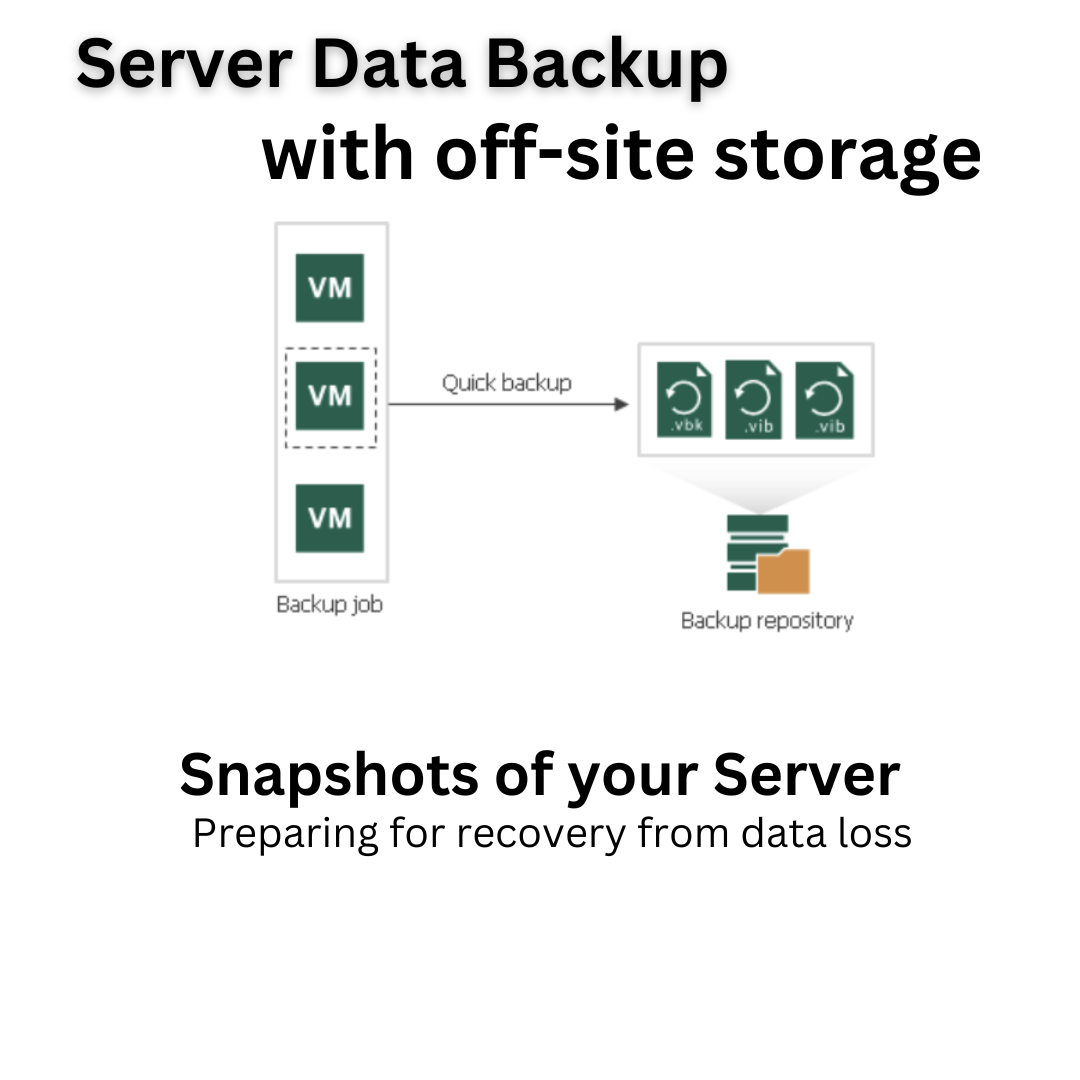
Ensuring Business Continuity with Server Backup and Replication: Backing up and replicating server data is crucial for maintaining business operations, allowing for rapid recovery and minimal downtime in the event of a server crash, data corruption, or other disasters.

Mitigating Threats with Risk and Compliance Scanning: Regular risk and compliance scanning helps identify vulnerabilities and ensures adherence to industry regulations, reducing the likelihood of security breaches and costly compliance violations.
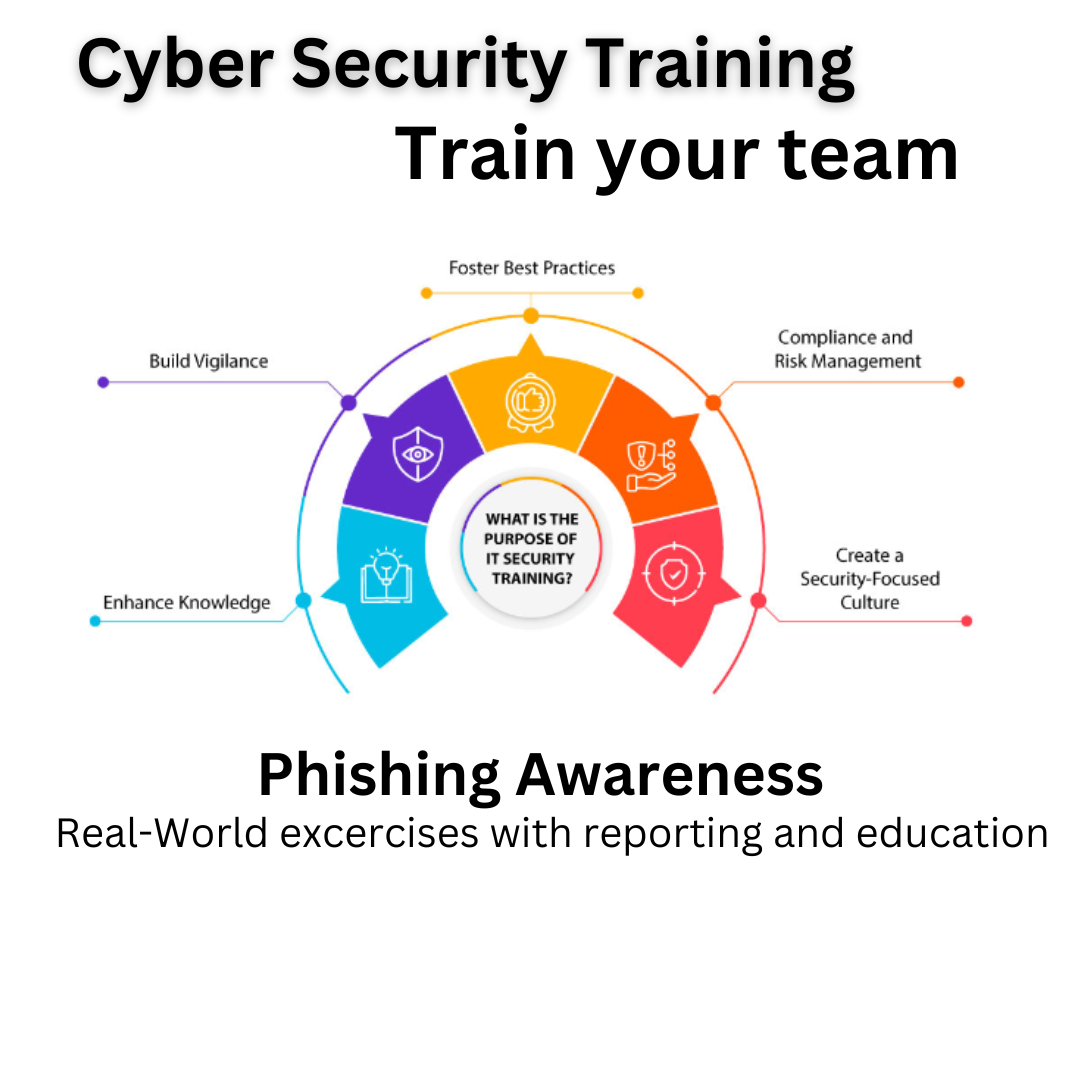
Strengthening Defense through End User Training: Cybersecurity training for end users equips employees with the knowledge to recognize and avoid potential threats, significantly reducing the risk of human error and enhancing overall organizational security.

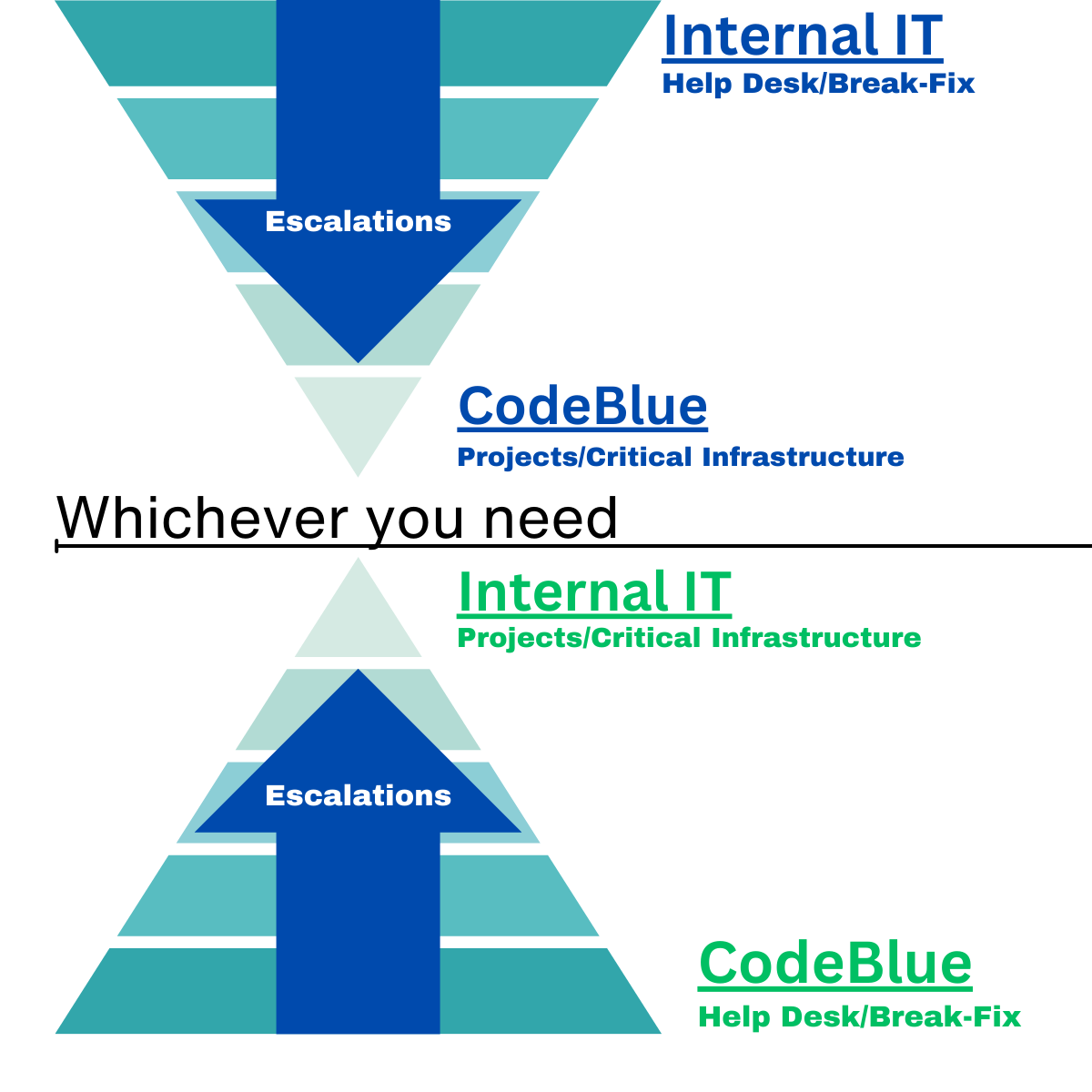
Managed Technology Plans
Your Managed Care team reviews for backup completion, health and success daily.
Co-Managed IT Services
The Importance of a Written Information Security Plan
Protecting Sensitive Information: A well-defined cybersecurity policy ensures that all staff, vendors, and partners follow strict guidelines for handling sensitive data, reducing the risk of data breaches and unauthorized access.
Standardizing Security Practices: Implementing a cybersecurity policy creates a consistent approach to security across the organization, ensuring that everyone is aware of their responsibilities and follows best practices to mitigate risks.
Compliance with Legal and Regulatory Requirements: A comprehensive cybersecurity policy helps businesses meet industry regulations and legal obligations, avoiding penalties and maintaining trust with clients and stakeholders.
Reducing Human Error and Insider Threats: By clearly outlining security protocols and expectations, a cybersecurity policy minimizes the chances of accidental or intentional security breaches caused by employees, vendors, or partners.